Keywords: information security, 5G, D2D
References
1. Adams C., Lloyd S. Understanding PKI: Concepts, Standards, and Deployment Considerations. 2nd ed. Addison-Wesley Professional, 2003, 322 p.
2. Boronin P.N., Kucheryavy A.E. Internet of Things as a new concept of the telecommunication networks development. Informatsionnye Tekhnologii i Telekommunikatsii, 2014, no. 3, pp. 7–30. (In Russian)
3. Haas Z.J., Deng J., Liang B., Papadimitratos P., Sajama S. Wireless Ad Hoc Networks. Encyclopedia of Telecommunications. John Wiley and Sons, 2002.
4. Muthanna S., Kucheryavy A.E. D2D-communication in the 5G mobile networks. Informatsionnye Tekhnologii i Telekommunikatsii, 2014, no. 4, pp. 51–63.(In Russian)
5. Khalili A., Katz J., Arbaugh W.A. Toward secure key distribution in truly ad-hoc networks.
Proc. Symposium on Applications and the Internet Workshops, 2003, pp. 342–346. doi:
10.1109/saintw.2003.1210183
6. Yi X., Willemson J., Nait-Abdesselam F. Privacy-preserving wireless medical sensor network.
Proc. 12th IEEE Int. Conf. on Trust, Security and Privacy in Computing and Communications (TrustCom), 2013, pp. 118–125. doi:
10.1109/trustcom.2013.19
7. Omjotov A.Ya., Kucheryavy A.E., Andreev S.D. About the wireless technology role for the development of ”Internet of Things”. Informatsionnye Tekhnologii i Telekommunikatsii, 2014, no. 3, pp. 31–40. (In Russian)
8. Lu Q., Miao Q., Fodor G.,Brahmi N. Clustering schemes for D2D communications under partial/no network coverage. IEEE 79th Vehicular Technology Conference (VTC Spring), 2014, pp. 1–5.
9. Perrig A., Stankovic J., Wagner D. Security in wireless sensor networks.
Communications of the ACM, 2004, vol. 47, no. 6, pp. 53–57. doi:
10.1145/990680.990707
10. McDaniel P., McLaughin S. Security and privacy challenges in the smart grid.
IEEE Security &Privacy Magazine, 2009.vol. 7, no. 3, pp. 75–77. doi:
10.1109/msp.2009.76
11. Hubaux J.-P., Capkun S., Luo J. The security and privacy of smart vehicles.
IEEE Security & Privacy Magazine, 2004, vol. 2, no. 3, pp. 49–55. doi:
10.1109/msp.2004.26
12. Diffie W., Hellman M.E.New directions in cryptography.
IEEE Transactions on Information Theory, 1976, vol. 22, no. 6, pp. 644–654. doi:
10.1109/tit.1976.1055638
13. Liu D., Ning P., Li R., Establishing pairwise keys in distributed sensor networks.
ACM Transactions on Information and System Security, 2005, vol. 8, no. 1, pp. 41–77. doi:
10.1145/1053283.1053287
14. Shamir A. How to share a secret.
Communications of the ACM, 1979, vol. 22, no. 11, pp. 612–613. doi:
10.1145/359168.359176
15. Shamir A. Identity-based cryptosystems and signature schemes.
Lecture Notes in Computer Science, 1985, vol. 196, pp. 47–53. doi:
10.1007/3-540-39568-7_5
16. Perrig A., Szewczyk R., Tygar J., Wen V., Culler D.E. SPINS: Security protocols for sensor networks.
Wireless Networks, 2002, vol. 8, no. 5, pp. 521–534. doi:
10.1023/a:1016598314198
17. Du W., Deng J., Han Y.S., Varshney P.K., Katz J., Khalili A. A pairwise key predistribution scheme for wireless sensor networks.
ACM Transactions on Information and System Security, 2005, vol. 8, no. 2, pp. 228–258. doi:
10.1145/1065545.1065548
18. Zhu S., Setia S., Jajodia S. LEAP+: Efficient security mechanisms for large-scale distributed sensor networks.
ACM Transactions on Sensor Networks, 2006. vol. 2, no. 4, pp. 500–528. doi:
10.1145/1218556.1218559
19. Zimmermann P. Why I wrote PGP. Part of the Original PGP User's Guide, 1991.
20. Zhou L., Haas Z.J.Securing ad hoc networks.
IEEE Network, 1999, vol. 13, no. 6, pp. 24–30. doi:
10.1109/65.806983
21. Bezzateev S.V., Stepanov M.V. Sets, free of coatings, constructed using elliptic codes. Nauchnyi Vestnik Noril'skogo Industrial'nogo Instituta, 2007, no. 1, pp. 74–75.(In Russian).
22. Bezzateev S., Stepanov M. Algebraic-geometry codes on Griesmer bound. Proc. of Algebraic and Combinatorial Coding Theory, ACCT-10. Zvenigorod, Russia, 2006, pp. 256–258.
23. Du X., Wang Y., Ge J., Wang Y. An ID-based broadcast encryption scheme for key distribution.
IEEE Transactions on Broadcasting, 2005, vol. 51, no. 2, pp. 264–266. doi:
10.1109/tbc.2005.847600
24. Chiou G.-H., Chen W.-T. Secure broadcasting using the secure lock.
IEEE Transactions on Software Engineering, 1989, vol. 15, no. 8, pp. 929–934. doi:
10.1109/32.31350
25. Jakobsen T., Knudsen L.R.The interpolation attack on block ciphers.
Lecture Notes in Computer Science, 1997, pp. 28–40. doi:
10.1007/bfb0052332
26. McEliece R.J., Sarwate D.V.On sharing secrets and reed-solomon codes.
Communications of the ACM, 1981, vol. 24, no. 9, pp. 583–584. doi:
10.1145/358746.358762
27. Man C.W.,Safavi-Naini R. Democratic key escrow scheme.
Lecture Notes in Computer Science, 1997, vol. 1270, pp. 249–260. doi:
10.1007/bfb0027932
28. Yuan J., Ding C.Secret sharing schemes from three classes of linear codes.
IEEE Transactions on Information Theory, 2006, vol. 52, no. 1, pp. 206–212. doi:
10.1109/tit.2005.860412
29. Massey J.L.Minimal codewords and secret sharing. Proc. 6th Joint Swedish-Russian International Workshop on Information Theory. Citeseer, 1993, pp. 276–279.
30. Lee K.H., Jung T., Krouk E., Bezzateev S., Linsky E. Weighted Secret Sharing and Reconstructing Method. Patent US 7551740, 2009.
31. Denning D.E.A lattice model of secure information flow.
Communications of the ACM, 1976, vol. 19, no. 5, pp. 236–243. doi:
10.1145/360051.360056
32. McEliece R. A public-key cryptosystem based on algebraic coding theory. DSN Progress Report, 1978, pp. 42–44.
33. Westfeld A. F5—A steganographic algorithm.
Lecture Notes in Computer Science, 2001, pp. 289–302. doi:
10.1007/3-540-45496-9_21
34. Bezzateev S., Voloshina N., Zhidanov K. Multi-level significant bit (MLSB) embedding based on weighted container model and weighted F5 concept.
Proc. 2nd Int. Afro-European Conference for Industrial Advancement AECIA, 2015, pp. 293–303. doi:
10.1007/978-3-319-29504-6_29
35. Bezzateev S., Voloshina N. The digital fingerprinting method for state images based on weighted Hamming metric and on weighted container model.
Journal of Computer and Communications, 2014, vol. 2, no. 9, pp. 121–126. doi:
10.4236/jcc.2014.29016
36. Voloshina N., Zhidanov K., Bezzateev S. Optimal weighted watermarking for still images. Proc. XIV Int. Symposium on Problems of Redundancy in Information and Control Systems. St. Petersburg, 2014, pp. 98–102.
37. Ometov A., Olshannikova E., Masek P., Olsson T., Hosek J., Andreev S., Koucheryavy Y. Dynamic trust associations over socially-aware D2D technology: a practical implementation perspective.
IEEE Access, 2016, vol. 4, pp. 7692–7702. doi:
10.1109/access.2016.2617207
38. Brockmann D., Hufnagel L., Geisel T. The scaling laws of human travel.
Nature, 2006, vol. 439, no. 7075, pp. 462–467. doi:
10.1038/nature04292
Rhee I., Shin M., Hong S., Lee K., Kim S.J., Chong S. On the Levy-walk nature of human mobility.
Proc. IEEE INFOCOM 2008 - The 27th Conference on Computer Communications, 2011,vol. 19, no. 3, pp. 30–43. doi:
10.1109/infocom.2008.145
PICTURES
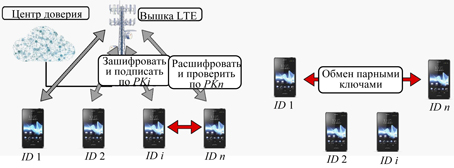
Fig. 1. Secure data transfer in the presence/absence of Public Key Infrastructure: PKi, PKn arethe public keys, IDis the unique device identifier, i, n – the sequence numbers of the device
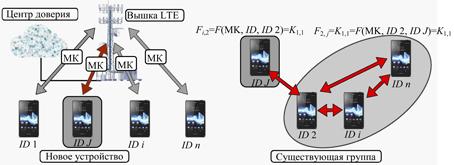
Fig. 2. The distribution of keys, where MK is the master key, and J is the ordinal number of the new device
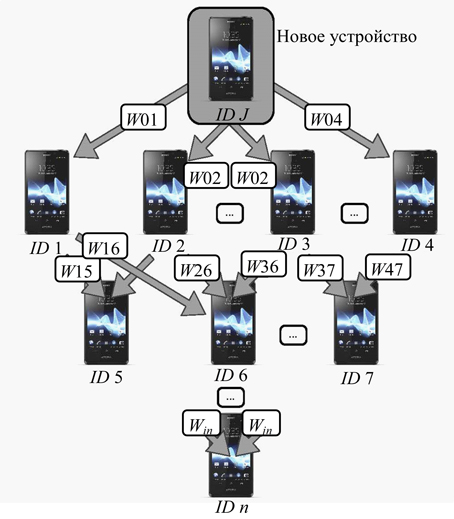
Fig. 3. Trust policy based on Pretty Good Privacy: Wij is the trust level between nodesi andj
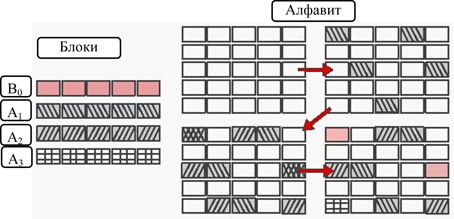
Fig. 4. Cover-Free Family for r = 2, n = 5
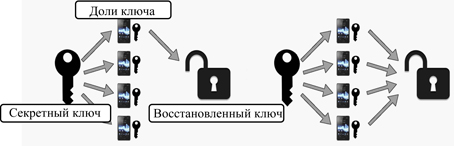
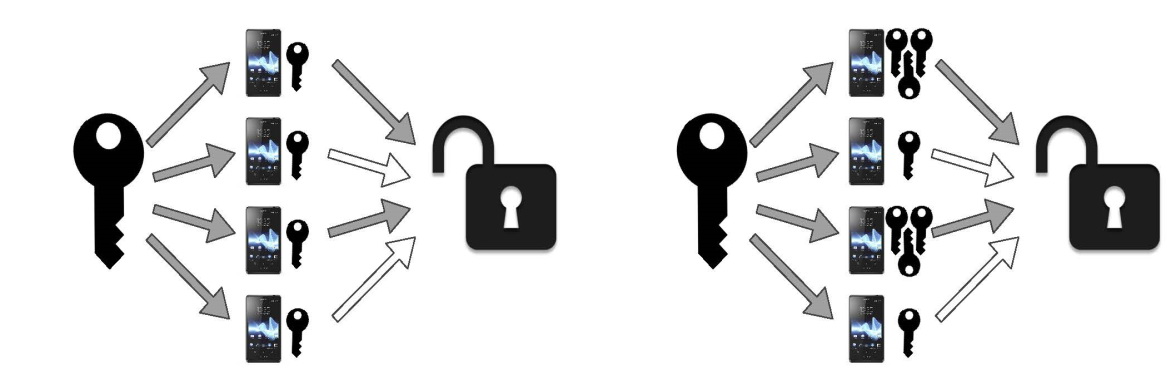
Fig. 5. Examples of key distribution schemes (a–d)
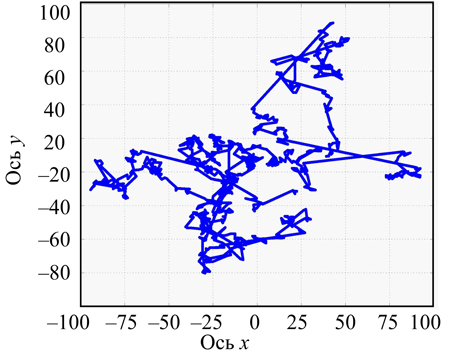
Fig. 6. An example of individual user movement in the system
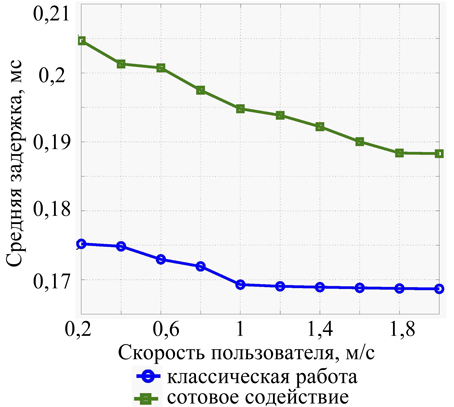
Fig. 7. The dependence of delay on the user’s speed
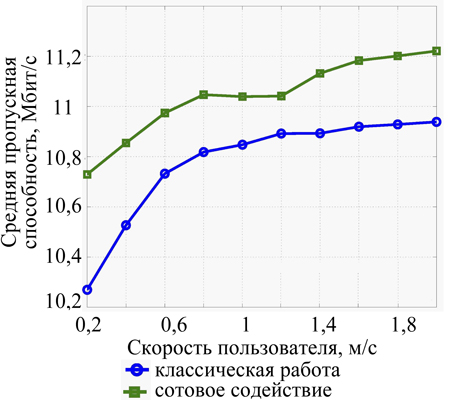
Fig. 8. The dependence of the throughput on the user’s speed